SD 6: Encryption - The Unsung Hero of Digital Security
Your All-in-One Utility Platform for Developers and Beyond 🚀
Imagine having access to dozens of essential tools in one place—no more switching tabs, searching for utilities, or dealing with daily limits. app.dailydev.in is your ultimate toolbox, offering solutions for developers, analysts, and tech enthusiasts alike.
Here’s what you’ll find:
Code Utilities: Format code, parse JWT, generate UUIDs, and more.
System Tools: Git commands, system utilities, epoch converters.
Data Transformers: YAML ↔ JSON, CSV ↔ JSON, Base64 encoders, and URL encoders.
Design Helpers: Color converters, CSS unit converters, image resizers, and HTML previews.
Analysis Tools: Diff checkers, hash generators, and UTM generators.
💡 Why Choose app.dailydev.in?
Free & Unlimited Access: No restrictions or daily limits.
User-Driven Features: Share feedback, report bugs, or request new tools—we’re here to build what you need.
Time-Saving: Simplify your workflow with everything you need in one platform.
Start exploring today and see how app.dailydev.in can transform your productivity.
Introduction:
In our hyper-connected world, data is the new gold. But unlike physical treasures locked away in vaults, our digital assets are constantly in transit, bouncing between devices and traversing the globe in milliseconds. So how do we keep this valuable information safe from prying eyes and malicious actors? The answer lies in encryption - the silent guardian of our digital realm.
As software engineers and tech enthusiasts, understanding encryption is crucial. It's the backbone of secure communication, data protection, and privacy in the digital age. In this deep dive, we'll unravel the mysteries of encryption, explore its inner workings, and discover why it's more relevant than ever in today's technology landscape.
What is Encryption?
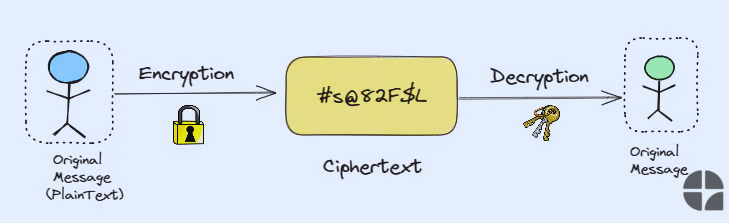
At its core, encryption is a process of encoding information in such a way that only authorized parties can access it. Think of it as a high-tech secret code that scrambles your data into an unreadable format. Without the right key to decode it, encrypted data looks like gibberish to anyone who intercepts it.
But encryption is far more than just a digital padlock. It's a sophisticated mathematical process that transforms plaintext (your original data) into ciphertext (the encrypted version) using complex algorithms and keys. This process ensures that even if someone manages to intercept your data, they can't make sense of it without the proper decryption key.
The Encryption Process: A Step-by-Step Breakdown
Plaintext: This is your original, readable data.
Encryption Algorithm: A mathematical formula that scrambles the plaintext.
Encryption Key: A unique string of bits used by the algorithm to encrypt the data.
Ciphertext: The scrambled, unreadable output of the encryption process.
Transmission: The ciphertext can now be safely sent over potentially insecure channels.
Decryption Key: The recipient uses this to reverse the encryption process.
Decryption Algorithm: Applies the key to the ciphertext to recover the original plaintext.
It's worth noting that in some encryption systems, the encryption and decryption keys are the same (symmetric encryption), while in others, they're different (asymmetric encryption). We'll dive deeper into these types later.
Why Encryption Matters
In an era of data breaches, identity theft, and digital espionage, encryption serves as our first line of defense. Here's why it's crucial:
Privacy Protection: Encryption keeps your personal communications, financial data, and sensitive information away from unauthorized eyes.
Data Integrity: It ensures that data hasn't been tampered with during transmission.
Authentication: Encryption can verify the identity of the sender, preventing impersonation attacks.
Regulatory Compliance: Many industries require encryption to meet data protection standards like GDPR, HIPAA, or PCI-DSS.
Trust in Digital Transactions: E-commerce, online banking, and digital signatures all rely on encryption for security.
As software engineers, we're often tasked with building systems that handle sensitive data. Understanding encryption allows us to implement robust security measures and protect our users' information effectively.
Types of Encryption
Not all encryption is created equal. Different scenarios call for different approaches. Let's explore the two main types of encryption:
Symmetric Encryption
Symmetric encryption uses the same key for both encryption and decryption. It's like a secret handshake known only to the sender and recipient.
Pros:
Fast and efficient, ideal for encrypting large amounts of data
Simpler to implement compared to asymmetric encryption
Cons:
Key distribution can be challenging, especially over insecure channels
Scalability issues in systems with many users, as each pair needs a unique shared key
Popular symmetric algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and Blowfish.
Example in Python using the cryptography library:
from cryptography.fernet import Fernet
# Generate a random symmetric key
key = Fernet.generate_key()
# Create a Fernet instance with the key
f = Fernet(key)
# Encrypt a message
message = b"Hello, World!"
encrypted = f.encrypt(message)
# Decrypt the message
decrypted = f.decrypt(encrypted)
print(f"Original: {message}")
print(f"Encrypted: {encrypted}")
print(f"Decrypted: {decrypted}")Asymmetric Encryption
Also known as public-key cryptography, asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. It's like a mailbox where anyone can drop in a letter (encrypt with the public key), but only the owner with the unique key can open it (decrypt with the private key).
Pros:
Solves the key distribution problem of symmetric encryption
Enables secure communication without prior key exchange
Supports digital signatures for authentication
Cons:
Slower than symmetric encryption, especially for large data sets
More computationally intensive
Popular asymmetric algorithms include RSA, ECC (Elliptic Curve Cryptography), and DSA (Digital Signature Algorithm).
Example in Python using the pycryptodome library:
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
import binascii
# Generate an RSA key pair
key = RSA.generate(2048)
private_key = key.export_key()
public_key = key.publickey().export_key()
# Encrypt a message with the public key
message = b"Hello, Asymmetric World!"
rsa_public_key = RSA.import_key(public_key)
rsa_public_key = PKCS1_OAEP.new(rsa_public_key)
encrypted = rsa_public_key.encrypt(message)
# Decrypt the message with the private key
rsa_private_key = RSA.import_key(private_key)
rsa_private_key = PKCS1_OAEP.new(rsa_private_key)
decrypted = rsa_private_key.decrypt(encrypted)
print(f"Original: {message}")
print(f"Encrypted: {binascii.hexlify(encrypted)}")
print(f"Decrypted: {decrypted}")Encryption in Action: Real-World Applications
Now that we understand the basics, let's explore how encryption is used in various real-world scenarios:
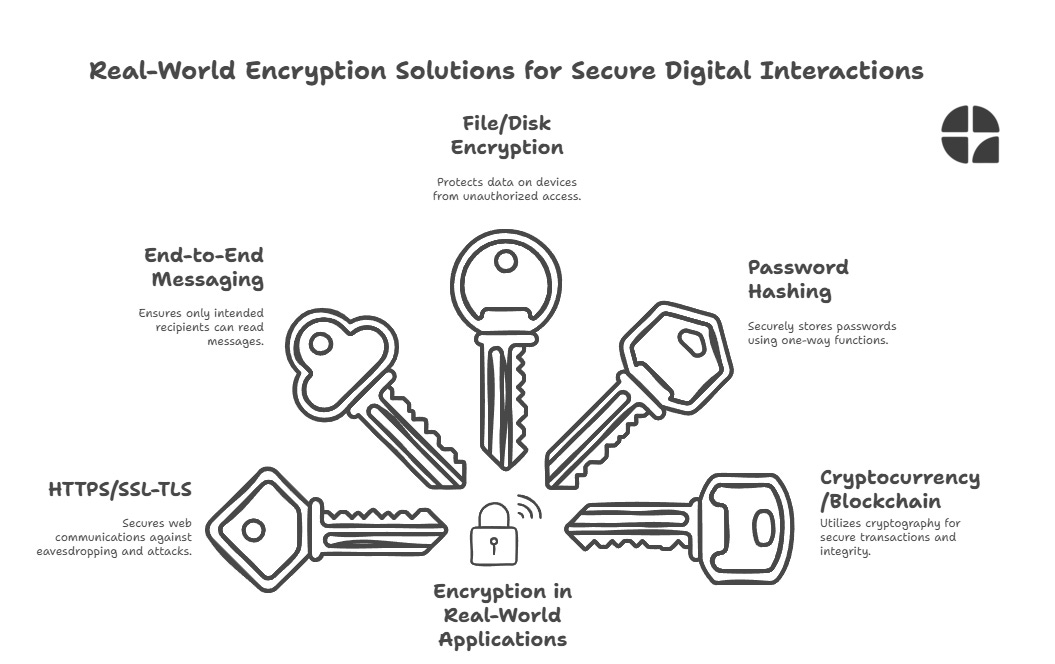
HTTPS and SSL/TLS When you see that little padlock in your browser's address bar, you're witnessing encryption in action. HTTPS uses SSL/TLS protocols to encrypt data transmitted between your browser and web servers, protecting against eavesdropping and man-in-the-middle attacks.
End-to-End Encrypted Messaging Apps like Signal and WhatsApp use end-to-end encryption to ensure that only the intended recipients can read messages. Even the service providers can't access the content of your communications.
File and Disk Encryption Tools like VeraCrypt or built-in options like BitLocker (Windows) and FileVault (macOS) use encryption to protect data stored on your devices. If your laptop is stolen, encrypted files remain inaccessible to thieves.
Password Hashing While not encryption in the traditional sense, password hashing uses one-way cryptographic functions to securely store user passwords. This ensures that even if a database is compromised, actual passwords remain protected.
Cryptocurrency and Blockchain The entire concept of cryptocurrencies like Bitcoin relies on cryptographic principles. Public-key cryptography is used for digital signatures and secure transactions, while hash functions maintain the integrity of the blockchain.
Challenges and Considerations in Encryption
While encryption is a powerful tool, it's not without its challenges:
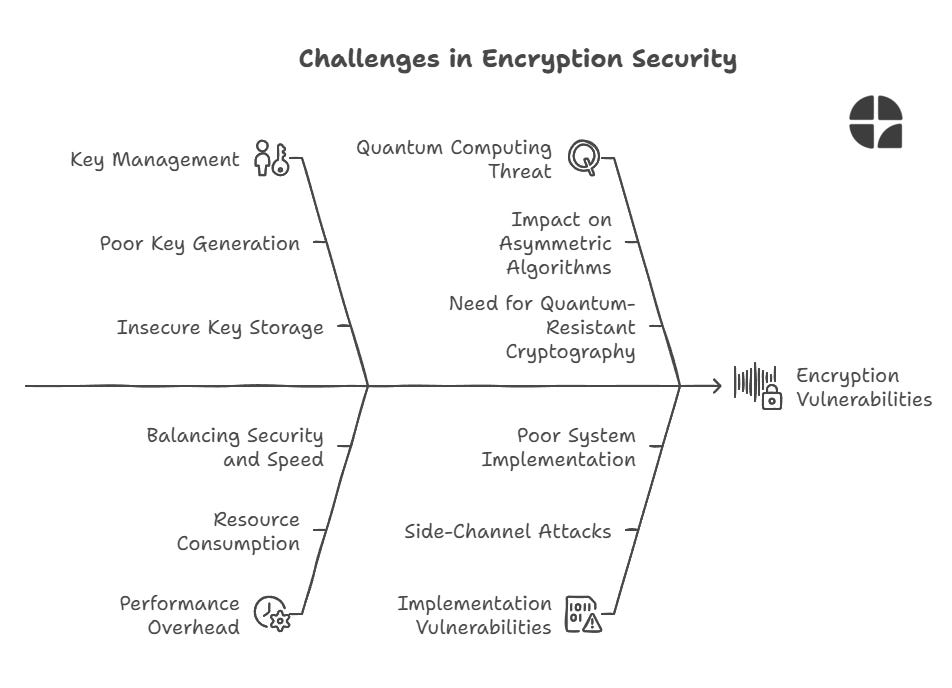
Key Management Securely generating, storing, and distributing encryption keys is crucial. Poor key management can undermine even the strongest encryption algorithms.
Performance Overhead Encryption and decryption processes consume computational resources. Balancing security with performance is an ongoing challenge, especially in resource-constrained environments.
Quantum Computing Threat The advent of quantum computers poses a potential threat to many current encryption methods, particularly asymmetric algorithms like RSA. This has led to research in quantum-resistant cryptography.
Legal and Ethical Considerations The use of strong encryption has sparked debates about privacy vs. national security, with some governments pushing for backdoors or key escrow systems.
Implementation Vulnerabilities Even with strong algorithms, poor implementation can lead to vulnerabilities. Side-channel attacks, for instance, can exploit the physical implementation of a cryptosystem rather than its mathematical properties.
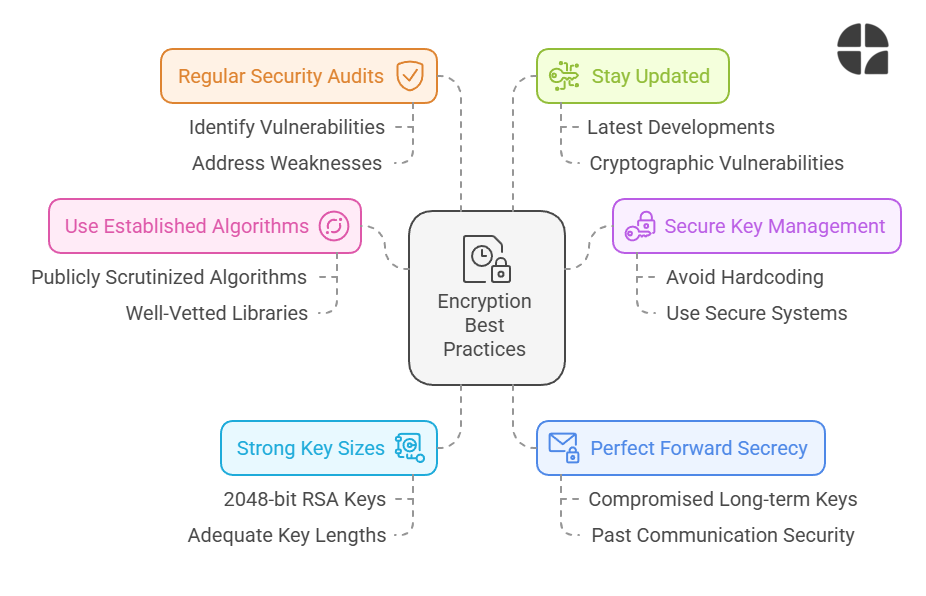
Best Practices for Implementing Encryption
As software engineers, we play a crucial role in implementing encryption correctly. Here are some best practices to keep in mind:
Use Well-Established Algorithms Don't roll your own crypto. Stick to well-vetted, publicly scrutinized algorithms and libraries.
Keep Encryption Keys Secure Use secure key management systems and avoid hardcoding keys in your source code.
Use Strong Key Sizes Ensure your key sizes are adequate for the level of security required. For instance, use at least 2048-bit keys for RSA.
Implement Perfect Forward Secrecy This ensures that even if long-term keys are compromised, past communications remain secure.
Regular Security Audits Conduct regular audits of your cryptographic implementations to identify and address any vulnerabilities.
Stay Updated Cryptography is an evolving field. Stay informed about the latest developments, vulnerabilities, and best practices.
The Future of Encryption
As technology advances, so too does the field of cryptography. Here are some exciting developments to watch:
Post-Quantum Cryptography Researchers are developing new algorithms resistant to attacks by quantum computers. NIST is currently in the process of standardizing post-quantum cryptographic algorithms.
Homomorphic Encryption This revolutionary approach allows computations to be performed on encrypted data without decrypting it first, opening up new possibilities for secure cloud computing.
Blockchain and Decentralized Systems The principles of cryptography are being applied in innovative ways to create secure, decentralized systems beyond just cryptocurrencies.
Quantum Key Distribution Quantum physics principles are being used to create theoretically unbreakable encryption methods for key distribution.
Conclusion
Encryption is the unsung hero of our digital world, silently protecting our data and communications from prying eyes. As software engineers and tech enthusiasts, understanding encryption is not just about implementing security features - it's about being guardians of digital privacy and trust.
From the symmetric ciphers that secure our stored data to the asymmetric algorithms that enable secure internet communications, encryption touches every aspect of our digital lives. By mastering these concepts, we can build more secure systems, protect user data more effectively, and contribute to a safer digital ecosystem.
As we stand on the brink of new technological frontiers - quantum computing, AI, and beyond - the importance of robust encryption will only grow. It's an exciting time to be in this field, with new challenges and innovations emerging constantly.
So, the next time you see that little padlock in your browser or send an encrypted message, take a moment to appreciate the complex mathematics and ingenious algorithms working behind the scenes. And remember, as builders of the digital world, the responsibility of implementing and maintaining these crucial security measures falls to us.
Let's encrypt, protect, and innovate - for a more secure digital future.