SD 9: What is Hashing: From Basics to Advanced
Introduction
In today's digital age, data security and efficient data management are paramount concerns for developers and organizations alike. At the heart of many security and performance solutions lies a fundamental concept: hashing. Whether you're storing passwords, verifying file integrity, or optimizing database operations, understanding hashing is crucial for any software engineer.
What is Hashing?
Hashing is a process that transforms input data of arbitrary size into a fixed-size output value, typically a string of characters. Think of it as a one-way function that takes your data and creates a unique "fingerprint" or digest. This transformation is performed using specialized algorithms called hash functions.
Key Characteristics of Hashing:
Deterministic: The same input will always produce the same hash value
Fixed Output Size: Regardless of input size, the hash length remains constant
One-way Function: It's computationally infeasible to reverse the process
Avalanche Effect: Small changes in input create significantly different outputs
Why is Hashing Important?
1. Data Security
Password Storage: Instead of storing plain-text passwords, systems store their hash values
Digital Signatures: Ensuring message integrity and authenticity
Blockchain Technology: Maintaining chain integrity and mining operations
2. Performance Optimization
Fast Data Retrieval: O(1) time complexity for lookups
Efficient Data Deduplication: Identifying duplicate content
Caching Systems: Quick verification of cached content
Common Hashing Algorithms
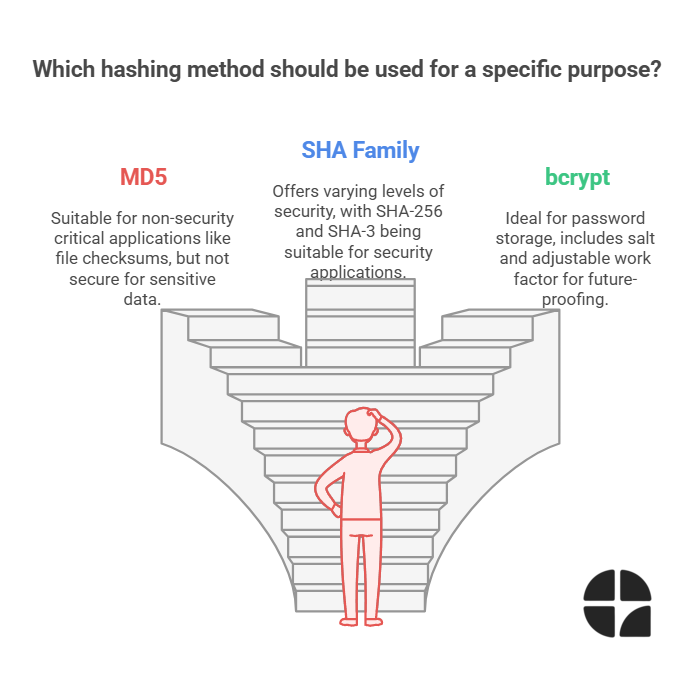
1. MD5 (Message Digest Algorithm 5)
128-bit hash value
Fast computation
Note: No longer considered cryptographically secure
Use cases: File checksums, non-security critical applications
2. SHA Family (Secure Hash Algorithm)
SHA-1: 160-bit hash (deprecated for security applications)
SHA-256: Part of SHA-2 family, widely used in security applications
SHA-3: Latest standard, offering improved security
3. bcrypt
Specifically designed for password hashing
Includes salt automatically
Adjustable work factor for future-proofing
Industry standard for password storage
Try hashing your content with different algorithms. You try online hashing tool and visualize how your output changes.
Handling Hash Collisions
Hash collisions occur when different inputs produce the same hash value. While unavoidable in theory, proper collision resolution is crucial for maintaining data structure efficiency.
Common Collision Resolution Techniques:
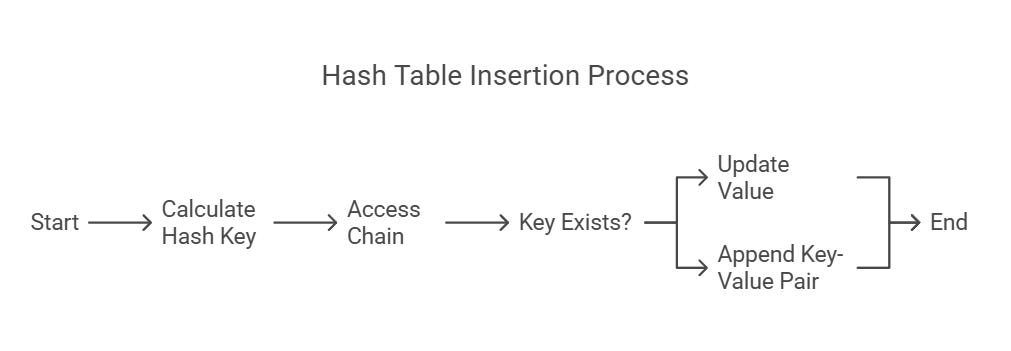
Separate Chaining
class HashTable:
def __init__(self, size):
self.size = size
self.table = [[] for _ in range(size)]
def insert(self, key, value):
hash_key = hash(key) % self.size
chain = self.table[hash_key]
for i, kv in enumerate(chain):
if kv[0] == key:
chain[i] = (key, value)
return
chain.append((key, value))Open Addressing
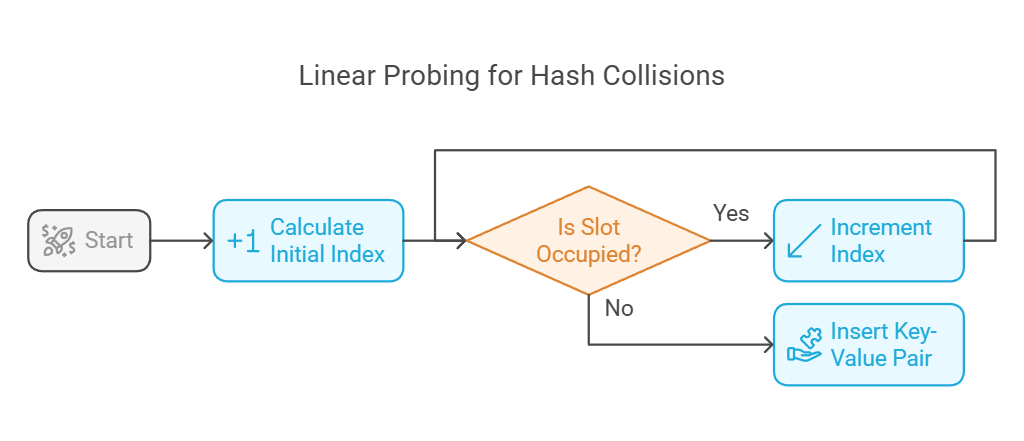
def linear_probe(hash_table, key, value):
size = len(hash_table)
index = hash(key) % size
while hash_table[index] is not None:
index = (index + 1) % size
hash_table[index] = (key, value)Real-world Applications
1. Git Version Control
Git uses SHA-1 hashes to identify commits and ensure data integrity. Each commit has a unique hash based on its contents and history.
2. Cryptocurrency
Bitcoin and other cryptocurrencies use hashing for:
Mining new blocks
Creating wallet addresses
Securing transactions
3. Content Delivery Networks (CDNs)
CDNs use content hashing to:
Cache management
Content verification
Deduplication
Best Practices for Implementing Hashing
Choose the Right Algorithm
# For passwords
import bcrypt
def hash_password(password):
salt = bcrypt.gensalt()
return bcrypt.hashpw(password.encode(), salt)
# For general data integrity
import hashlib
def hash_file(filename):
sha256_hash = hashlib.sha256()
with open(filename, "rb") as f:
for byte_block in iter(lambda: f.read(4096), b""):
sha256_hash.update(byte_block)
return sha256_hash.hexdigest()Implement Proper Salt Usage
import os
import hashlib
def create_salted_hash(data):
salt = os.urandom(32)
key = hashlib.pbkdf2_hmac(
'sha256',
data.encode('utf-8'),
salt,
100000
)
return salt + keyConsider Performance Requirements
from time import time
def benchmark_hash_function(hash_func, data, iterations=1000):
start_time = time()
for _ in range(iterations):
hash_func(data)
end_time = time()
return (end_time - start_time) / iterationsCommon Pitfalls to Avoid
Using Cryptographic Hashes for Passwords
Ignoring Collision Handling
Not Salting Sensitive Data
Using Deprecated Algorithms
Future of Hashing
The field of hashing continues to evolve with:
Quantum-resistant hashing algorithms
Improved performance optimizations
Enhanced security features
Conclusion
Hashing remains a fundamental concept in computer science, with applications spanning security, performance, and data integrity. As a software engineer, understanding and properly implementing hashing is crucial for building robust and secure applications.
Call to Action
Try online hashing tool with your content.
Audit your current hashing implementations
Update deprecated hashing algorithms
Implement proper security measures
Stay informed about new hashing developments
Additional Resources
Remember: The field of cryptography and hashing is constantly evolving. Stay updated with the latest security recommendations and best practices to ensure your implementations remain secure and efficient.